The Logic of Protection Approaches
Four Models to Safeguard Civilians from Harm

Every day, civilians suffer in violent conflicts. Attacks by armed forces, militias and rebel groups have left and continue to leave thousands dead or injured, and have resulted in the forced displacement of millions of people. To mitigate or end such violations, different actors – including NGOs, the UN, military forces, religious groups, and community leaders – often attempt to influence conflict parties to cease attacks on civilians and instead enhance their protection. Focusing on preventive protection efforts that hinder future harms (rather than mitigating the effects of past violations), we asked ourselves: How do protection actors plan and conduct these activities to reduce violence at the hands of combatants?
To find out, we posed this question to 148 staff members of various entities involved in preventive protection, including UN agencies, NATO and other armed forces, as well as civil society organizations conducting humanitarian, human rights and conflict management work. We also interviewed 23 academics working in international relations, conflict and peace studies, peacekeeping, legal studies, humanitarian studies, and human rights. In addition, we consulted academic literature and conducted two workshops to fine-tune our findings.
Based on our research, we identified four main approaches through which these protection actors influence how armed forces treat and behave toward civilians:
- “Naming and shaming” armed actors;
- Mobilizing influencers;
- Capacitating communities; and
- Training armed actors.
For each approach, we offer abstract models that break down the underlying logic, outlining how each method intends to change armed actor behavior – and how it can fall short of its goals or even backfire.
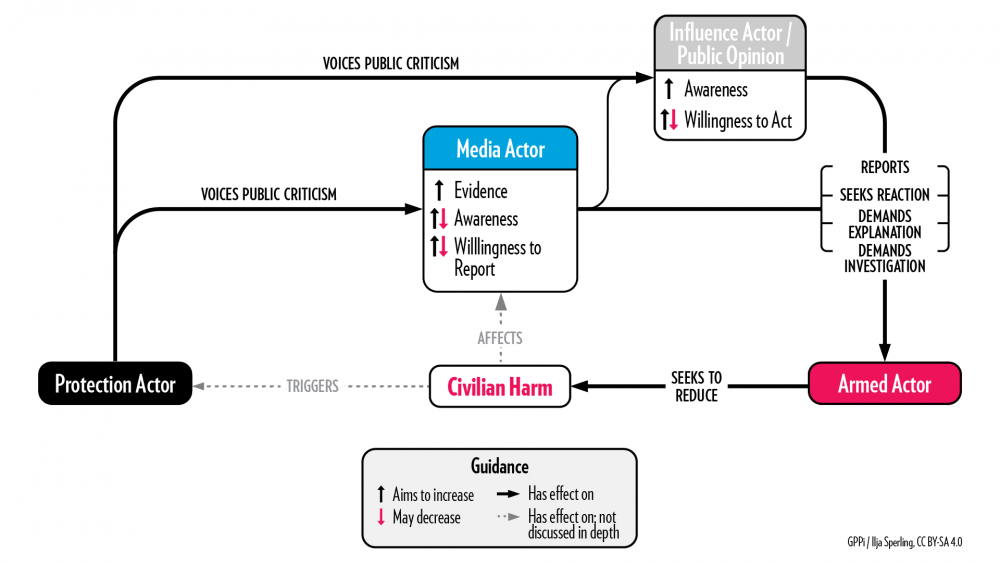
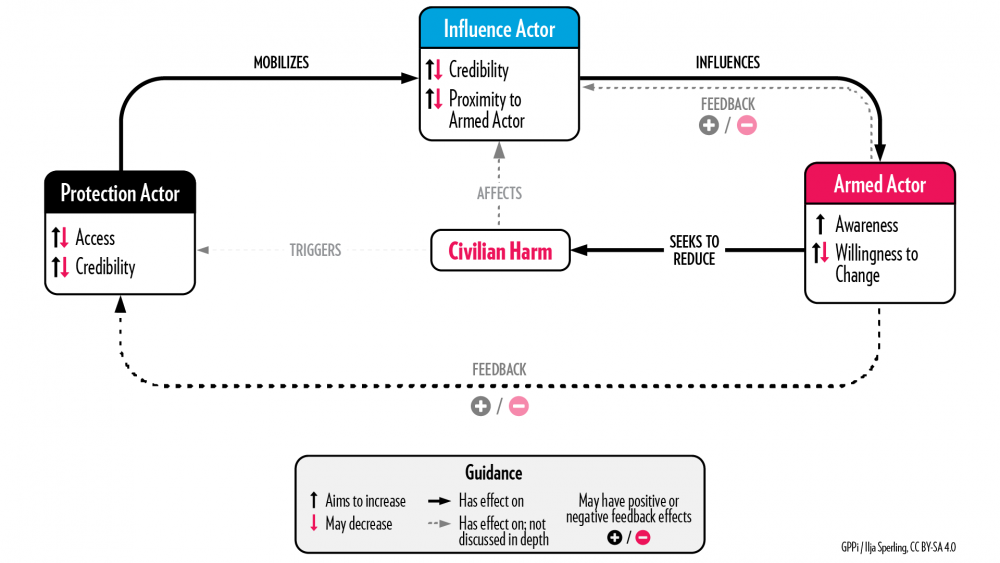
Approach 1: “Naming and Shaming” Armed Actors
Key logic: When media attention is brought to the harmful deeds of armed groups, pressure on them may increase enough to make them address the issue.
Real-life example: Releasing children from military imprisonment in Nigeria.
In 2019, a human rights organization published a report based on interviews with 32 children in Northeast Nigeria who had been imprisoned as suspected members of a non-state armed group. According to the organization, thousands of children had been held without charges, some for years. The government initially denied the report and disputed that it had detained children. However, within days of the report’s publication, the first children were released from the military barracks in which most of the interviewees had been held. According to the organization, the government freed more than 330 children during the six months following its report.
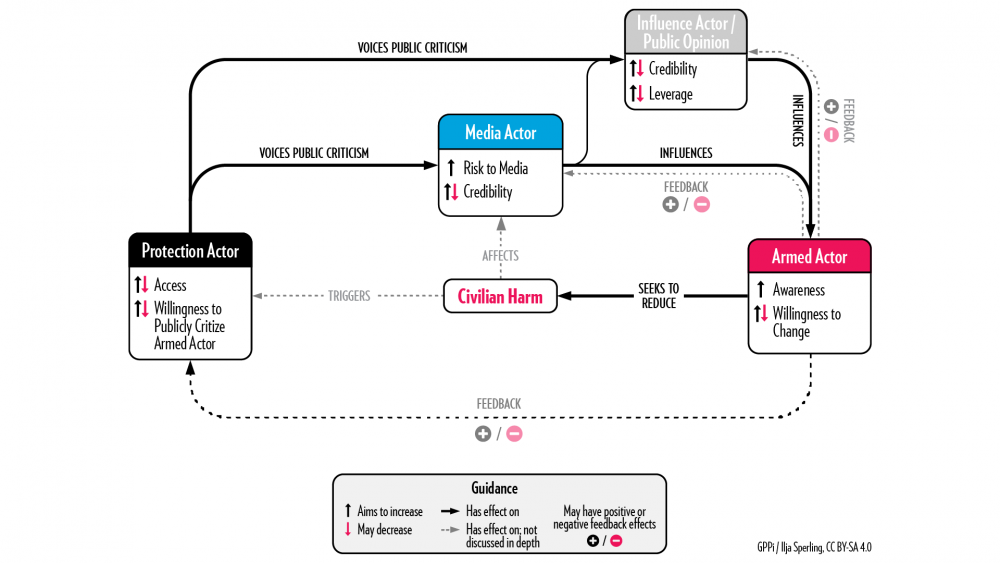
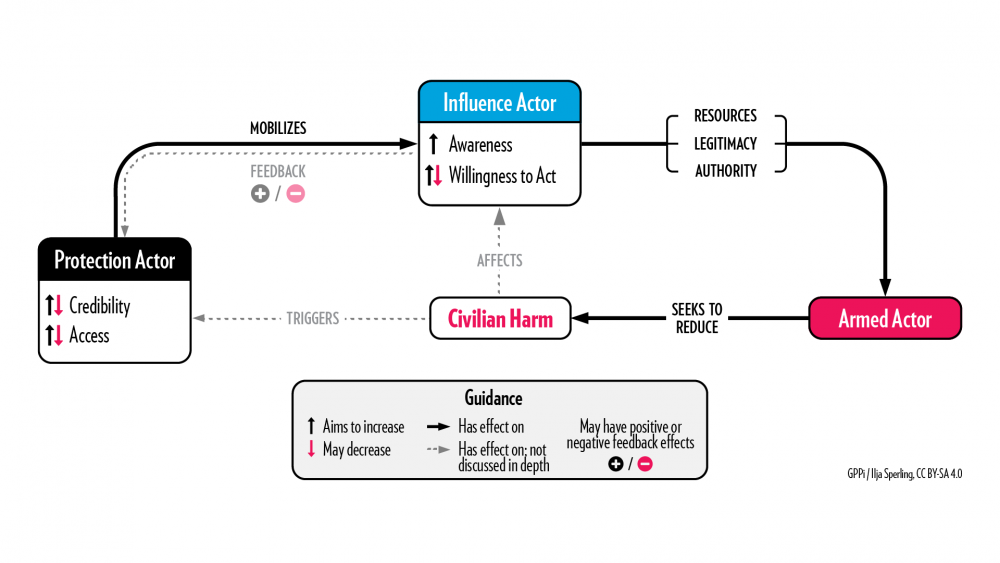
Approach 2: Mobilizing Influencers
Key logic: Convincing influencers to exert pressure on or persuade armed groups to change their harmful behavior can lead armed actors to improve their treatment of civilians.
Real-life example: Motivating tribal leaders to engage with an armed group in Yemen.
In Yemen, an international organization worked in close collaboration with its national staff to influence tribal leaders and community elders with close connections to a non-state armed group who had committed significant civilian harm. National staff attended traditional Qat chewing sessions and talked about humanitarian principles and protection concerns caused by the armed actor’s conduct toward civilians. The organization found that tribal leaders had a strong political interest in helping their communities and could therefore be motivated to convince the armed group to improve its behavior.
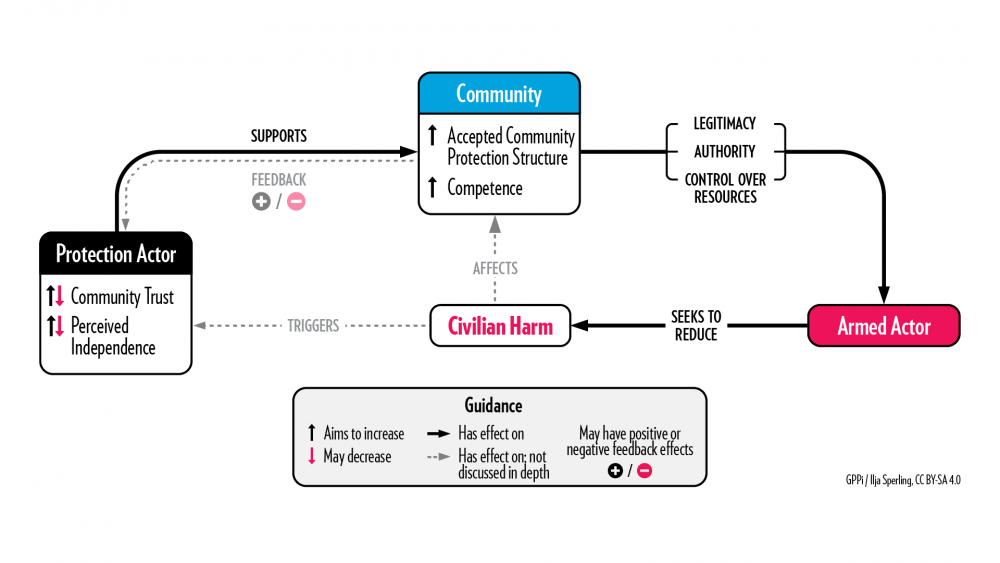
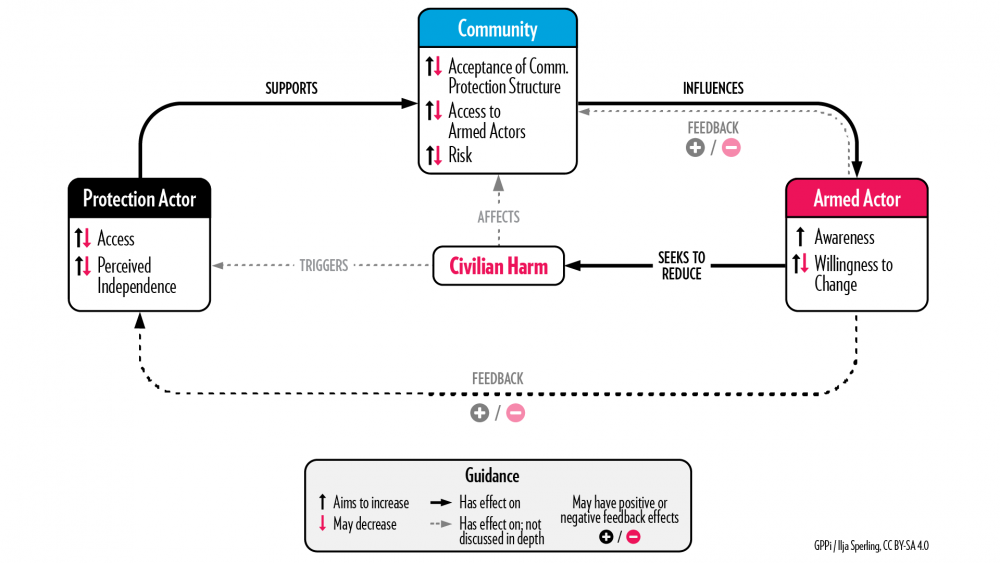
Approach 3: Capacitating Communities
Key logic: The protection actor supports communities so that they may make better use of their capacities to influence the armed actor’s behavior toward them.
Real-life example: Enabling communities to cooperate with armed forces on addressing crime in South Sudan.
In 2019, communities in Mundri East County in South Sudan complained about harassment, physical abuse and even torture at the hands of armed forces, who were trying to deal with a spate of armed robberies in the area. Both sides blamed each other for the criminal incidents. Too afraid to engage the armed forces directly, community leaders sought support from a non-partisan peacebuilding organization operating in the area. The local team facilitated an open dialogue between the civilians and the armed forces and conducted unarmed patrols in areas particularly affected by criminal incidents. The protection actor regularly met with community leaders and armed forces, encouraging them to work together to maintain peace and stop violence against civilians. It reported that six months after it first became involved, communities said that their relationship with the soldiers had improved and that there had been no recent incidents of harassment. The overall number of criminal incidents had also decreased, and the protection actor was told that communities and soldiers had agreed to deal with the crime problem through dialogue.
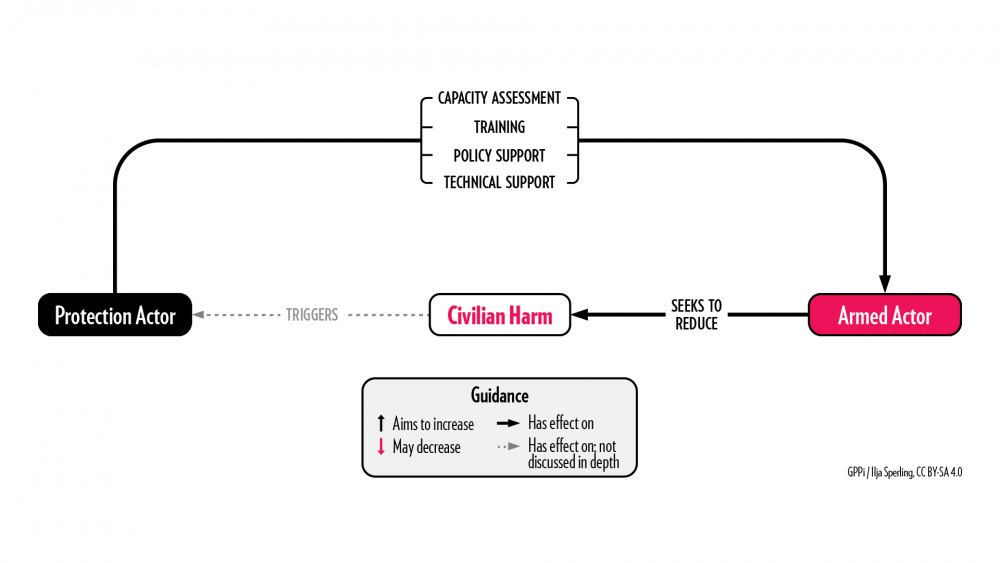
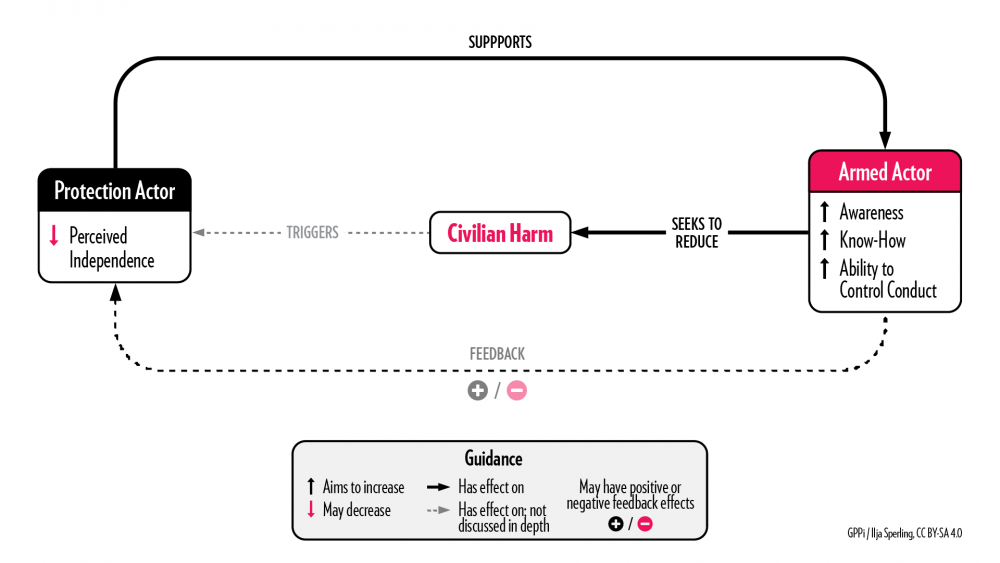
Approach 4: Training Armed Actors
Key logic: The protection actor helps an armed group who has expressed willingness to change its behavior understand which structural factors lead to civilian harm and addresses them through training and technical support.
Real-life example: Training officers at checkpoints in Yemen.
A protection actor regularly trained front line soldiers in Yemen on the protection of civilians during military operations. One of the trainees later passed on to other soldiers what he had learned, including to an officer who had regularly shot at civilian cars that sped through checkpoints without stopping. During a follow-up visit by the training instructor, a car sped through the checkpoint, but the officer did not shoot. Instead, he called the next checkpoint and asked them to stop the vehicle to find out why it did not stop before. Typically, drivers said that they had not seen signs indicating a checkpoint or understood that they needed to stop the car. In this instance, when the instructor asked why the officer did not shoot, he replied that the protection actor had taught him not to shoot.
Want to learn more about the logic models? Our research report delves into the different steps involved in each of these protection approaches.
We also created a user guide that outlines the practical use cases for our findings. We hope that this user guide can help organizations understand what type of analysis they should conduct before deciding whether to engage in preventive protection and which approach they should choose. The logic models can also help practitioners identify the risks associated with each approach and pinpoint the indicators they can use to check whether their intervention is on the right track. In doing so, the logic models serve an additional purpose: facilitating the creation of synergies between different protection actors and complementary approaches.
The full report and user guide are available for download.
This research project has been made possible by the generous support of UK Research and Innovation and the UK Foreign, Commonwealth & Development Office. To conduct our research, we partnered with the Institute of Regional and International Studies at the American University of Iraq as well as with Geneva Call and the Norwegian Refugee Council.
The logic models in this publication were conceptualized with and created by Ilja Sperling.